jwSpamSpy Recent spam domains Spam domain blacklist
Links joewein.de joewein.net Contact |
|
|
Phishing for your wallet: Suspicious mails involving Citibank, eBay, PayPal, etc.
- What is 'phishing'
- What you can do
- Example of 'phishing'
- 'phishing' links
- Fake T-Com invoice (phishing)
As more people use computers for handling financial transactions, from online banking to purchasing or selling goods at eBay, fraudsters have started use cleverly disguised spam to harvest information that allows them to break into online accounts and steal money.
Mails that typically claim to be from Citibank, eBay, PayPal or other banks state that because of some problem the recipient needs to confirm his/her access codes or his/her account will be suspended. This threat is supposed to scare people into acting rashly, without thinking.
Some of these emails look almost exactly like the real thing, complete with company logos, etc. Don't fall for it! Citibank, PayPal and other financial institutions never contact their customers supplying a link for re-entering their account numbers, passwords or PIN-codes. Though the links lead to websites that look like official company websites and in some cases even the browser displays a matching URL, these sites are in fact put up by fraudsters and are usually hosted on servers in China. It is suspected that Russian organized crime groups are the main operators of this type of scam.
|
What you can do
If you receive such emails, either disregard them or forward them to the security departments of the institutions they claim to originate from. You can also forward the messages (with full headers!) to email address
postmaster at corp.mailsecurity.net.auwhich feeds them into a database used for blocking spams.
Example of 'phishing' scam:
On July 2 I received the following message:
From: "Support" <cash@citibank.com>The sender address looks like Citibank and the link appears to lead to Citibank's website. If you click on the link, you get a site that looks like a genuine Citibank website:
To: <joewein@pobox.com>
Sent: Friday, 02 July, 2004 0:01
Subject: Please confirm your account details with Citibank!
Dear Customer,
This email was sent by the Citibank server to verify your E-mail
address. You must complete this process by clicking on the link
below and entering in the small window your Citibank Debit
Card number and PIN that you use on ATM.
This is done for your protection - because some of our members
no longer have access to their email addresses and we must
verify it.
To verify your E-mail address and access your bank account,
click on the link below:
https://wwww.citibank.com/signin/confirmation.jsp
---------------------------------------
Thank you for being our customer
---------------------------------------
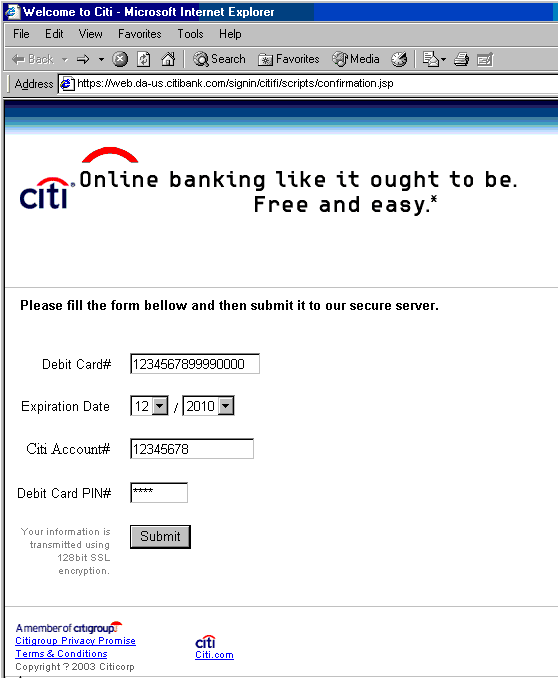
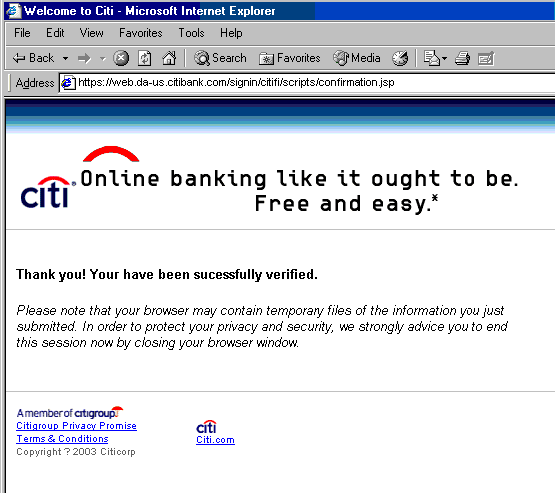
If you fill in totally bogus numbers and click submit, the site will accept them without complaint, as it does not verify them but only forwards them to the criminals...
If you look at message source code (Ctrl+F3 in Outlook Express), you will see that it was sent from a machine accessing via an Italian phone company and the website link actually goes to the URL http://219.148.127.67/scripts/confirmation.htm.
Return-path: <cash@citibank.com>
Envelope-to: joewein@pobox.com
Received: from host90-236.pool81117.interbusiness.it (host90-236.pool81117.interbusiness.it [81.117.236.90])
by kelvin.pobox.com (Postfix) with SMTP id C3D8A184DA9;
Thu, 1 Jul 2004 10:20:13 -0400 (EDT)
X-Message-Info: PVHpdpBRT386vYQ73DgUJ038RDhxWYP334B093EU54gvc2GW
Received: (from r63leaven@localhost)
by jz703-create931.yph51e.hotmail.com (6.42.66/9.40.36) id s797C55j51593;
Thu, 01 Jul 2004 17:06:30 +0200 GMT
X-Authentication-Warning: hvy27-bombast1.egf59ofb.hotmail.com: fs950decision set sender to cash@citibank.com using -u
MIME-Version: 1.0
Date: Thu, 01 Jul 2004 14:01:30 -0100
From: Support <cash@citibank.com>
Subject: Please confirm your account details with Citibank! To: joewein@pobox.com
Message-Id: <mk891lrr282-565696110917656-85715486442173513960083794653@fischbein26>
Content-Type: multipart/alternative; boundary="--63924826445955534931"
----63924826445955534931
Content-Type: text/html;
Content-Transfer-Encoding: quoted-printable
<P>Dear Customer,</P>
<P><BR>This email was sent by the Citibank server to verify your E-mail<BR=
>address. You must complete this process by clicking on the link<BR>below =
and entering in the small window your Citibank Debit<BR>Card number and PI=
N that you use on ATM.</P>
<P><BR>This is done for your protection - because some of our members<BR>n=
o longer have access to their email addresses and we must<BR>verify it.</P=
>
<P><BR>To verify your E-mail address and access your bank account,<BR>clic=
k on the link below:</P><A href=3D"http://219.148.127.67/scripts/confirmat=
ion.htm">https://wwww.citibank.com/signin/confirmation.jsp</A></A>
<P></P>
<P><BR>---------------------------------------</P>
<P>Thank you for being our customer</P>
<P>---------------------------------------</P>
----63924826445955534931--
'Phishing'-site hosted in China (China Telecom):
The actual scam website address (http://219.148.127.67/scripts/confirmation.htm) was still working two days after we received the spam email. The site is hosted by the following network:
inetnum: 219.148.0.0 - 219.148.159.255
netname: CHINATELECOM-he
descr: CHINANET hebei province network
descr: China Telecom
descr: No.31,jingrong street
descr: Beijing 100032
country: CN
admin-c: CH93-AP
tech-c: BR3-AP
mnt-by: MAINT-CHINANET
mnt-lower: MAINT-CHINATELECOM-he
changed: hostmaster@ns.chinanet.cn.net 20030820
status: ALLOCATED NON-PORTABLE
source: APNIC
person: Chinanet Hostmaster
address: No.31 ,jingrong street,beijing
address: 100032
country: CN
phone: 10-66027112
fax-no: 10-58501144
e-mail: hostmaster@ns.chinanet.cn.net
e-mail: anti-spam@ns.chinanet.cn.net
nic-hdl: CH93-AP
mnt-by: MAINT-CHINANET
changed: hostmaster@ns.chinanet.cn.net 20021016
remarks: hostmaster is not for spam complaint,please send spam
complaint to anti-spam@ns.chinanet.cn.net
source: APNIC
person: Bin Ren
nic-hdl: BR3-AP
e-mail: renbin@mail.he.cn
address: 10F Ximei Building NO.6 Jianshe South Street
address: Shijiazhuang 050011 China
phone: 311-5211551
fax-no: 311-5211578
country: CN
changed: renbin@mail.he.cn 20040430
mnt-by: MAINT-CHINATELECOM-HE
source: APNICWhen we checked on 2004-07-20, a total of 19 days after the initial email, the fraud website (http://219.148.127.67/scripts/confirmation.htm) was still active on the Chinanet server. It opens the real Citibank website, which shows a trustworthy-looking page with Citibank URL, but then pops up a window without URL line that runs a PHP script.
<!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.01 Transitional//EN">
<html>
<head>
<title>Citibank</title>
<meta http-equiv="Content-Type" content="text/html; charset=iso-8859-1">
<script language="JavaScript" type="text/javascript">
<!-- Hide script from older browsers
setTimeout ("changePage()", 0);
function changePage() {
if (self.parent.frames.length != 0)
self.parent.location=document.location;
}
// end hiding contents -->
</script>
<meta http-equiv="refresh"
content="0;URL=https://web.da-us.citibank.com/cgi-bin/citifi/scripts/myciti/support.jsp">
<SCRIPT LANGUAGE="JavaScript">
<!--begin
{
window.open('pop.php','MyWindow','scrollbars=no,resizable=no,toolbar=no,
width=350,height=430,left=350,top=200');
}
// end -->
</SCRIPT>
</head>
<body>
</body>
</html>
Here is the PHP script for the child window:
<html>
<head>
<meta http-equiv="Content-Type" content="text/html; charset=windows-1252">
<title>Citibank - Confirm your identity</title>
<script language="JavaScript" type="text/JavaScript">
<!--
function MM_reloadPage(init) { //reloads the window if Nav4 resized
if (init==true) with (navigator) {if ((appName=="Netscape")&&(parseInt(appVersion)==4)) {
document.MM_pgW=innerWidth; document.MM_pgH=innerHeight; onresize=MM_reloadPage; }}
else if (innerWidth!=document.MM_pgW || innerHeight!=document.MM_pgH) location.reload();
}
MM_reloadPage(true);
//-->
</script>
<style type="text/css">
<!--
.default
{
font-family: Arial, Helvetica, sans-serif;
font-size: 12px;
}
.defaultErr
{
font-family: Arial, Helvetica, sans-serif;
font-size: 11px;
color: #FF0000;
}
.style1 {font-family: Arial, Helvetica, sans-serif}
-->
</style>
</head>
<body topmargin="0" leftmargin="0" bgcolor="#FFFFFF">
<form name="Citi" method="post" runat="vdaemon" action="process.php">
<table width="350" height="61" border="0" align="center" cellpadding="0"
cellspacing="0" bordercolor="#111111" id="AutoNumber1"
style="border-collapse: collapse">
<tr>
<td height="36" background="http://www.citibank.co.uk/uk/images/wave_new.gif"></td>
</tr>
<tr>
<td width="100%" height="42" > <table width="350" height="42" border="0"
cellpadding="0" cellspacing="0">
<tr>
<td width="10" height="42"> </td>
<td width="340"><img src="http://www.citibank.co.uk/uk/images/logo3.gif"
width="96" height="42"></td>
</tr>
</table></td>
</tr>
</table>
<table width="350" border="0" align="center" cellpadding="0" cellspacing="0"
bordercolor="#111111" id="AutoNumber5" style="border-collapse: collapse">
<tr>
<td bgcolor="#CCCCCC"><img src="../images/trans.gif" width="1" height="1">
</td></font></td>
</tr>
</table>
<table width="350" border="0" align="center" cellpadding="3" cellspacing="0">
<tr>
<td height="22">
<div align="center"><b><font face="Arial, Helvetica, sans-serif" size="2">Please
update your ATM/Debit Card number</font></b></div>
</td>
</tr>
</table>
<table width="345" height="42" border="0" align="center" cellpadding="0" cellspacing="0">
<tr>
<td height="28">
<div align="center"><div class="defaultErr" id="VDaemonID_1"> </div>
</div></td>
</tr>
</table>
<table width="350" border="0" align="center" cellpadding="5" cellspacing="0"
bordercolor="#111111" id="AutoNumber4" style="border-collapse: collapse">
<tr>
<td align="right" width="106">
<div align="right"><font size="2" face="Arial, Helvetica, sans-serif">ATM/Debit
Card <br>
(CIN) / Card # </font></div>
</td>
<td width="224" align="left"><font face="Arial">
<input name="CardNumber" type="text" size="16" maxlength="16" />
</font><font face="Arial" size="1">
</font></td>
</tr>
<tr>
<td align="right" width="106">
<div align="right"><font size="2" face="Arial, Helvetica, sans-serif">ATM
PIN # </font></div>
</td>
<td align="left"><font face="Arial">
<input name="CurrentPIN" type="password" size="4" maxlength="4" />
</font><font face="Arial" size="1">
</font></td>
</tr>
<tr>
<td height="32" align="right" valign="top"><font size="2"
face="Arial, Helvetica, sans-serif">User
ID </font></td>
<td align="left" valign="top"><font face="Arial">
<input name="NewPIN" type="text" size="25" maxlength="25" />
</font></td>
</tr>
<tr>
<td height="56" align="right" valign="top"><font size="2"
face="Arial, Helvetica, sans-serif">Password
</font></td>
<td align="left" valign="top"><font face="Arial">
<input name="AccountNumber" type="password" id="AccountNumber"
size="25" maxlength="25" />
</font>
<div align="left" class="style1"><font size="1" color="#666666">To verify
your identity enter your login and<br>
password that you use to login on our site!</font></div>
<tr>
<td height="34" align="right" valign="top">
<div align="center" class="style1"></div>
</td>
<td align="left" valign="top"><font face="Arial" size="2">
<input name="Submit" type="image" id="Submit"
src="https://web-ao.da-us.citibank.com/images/univers/buttons/cont_btn.gif"
width="77" height="24" border="0" />
</font><font face="Arial"> </font>
</table>
<div align="left">
<table width="350" border="0" align="center" cellpadding="0" cellspacing="0"
bordercolor="#111111" id="AutoNumber5" style="border-collapse: collapse">
<tr>
<td bgcolor="#CCCCCC"><img src="../images/trans.gif" width="1" height="1"></td>
</tr>
</table>
</div>
<div align="left">
<table width="350" border="0" align="center" cellpadding="5" cellspacing="0"
bordercolor="#111111" id="AutoNumber6" style="border-collapse: collapse">
<tr>
<td width="163"><font face="Arial" size="1"><img border="0"
src="http://www.citibank.com/domain/images/mem_cgrp.gif" width="108" height="13"><br>
</font><font size="1"><span class="style1"><font color="#666666">
Copyright � 2004 Citicorp</font></span></font></td>
<td width="90"><div align="right"><font face="Arial" size="1" color="#666666">
<img src="https://www.citibank.com/us/cards/images/homepage/lock.gif"></font>
</div></td>
<td width="67"><div align="left" class="style1"><font size="1" color="#666666">
128bit SSL</font></div></td>
</tr>
</table>
</div>
<input type="hidden" name="VDaemonValidators"
value="O:13:"cvdvalruntime":5:{s:5:"sPage";s:16:"
/scripts/pop.php";s:5:"sArgs";s:0:"";s:7:"sAnchor";
s:0:"";s:5:"sForm";s:4:"Citi";s:6:"aNodes";
a:5:{i:0;O:7:"xmlnode":3:{s:5:"sName";s:11:"vlvalidator";
s:6:"aAttrs";a:4:{s:4:"name";s:13:"CardNumberReq";
s:4:"type";s:8:"required";s:7:"control";s:10:
"CardNumber";s:6:"errmsg";s:16:"Card # required.";}
s:9:"aSubNodes";a:0:{}}i:1;O:7:"xmlnode":3:{s:5:"sName";
s:11:"vlvalidator";s:6:"aAttrs";a:5:{s:4:"name";s:15:"
CardNumberCheck";s:4:"type";s:6:"custom";s:7:
"control";s:10:"CardNumber";s:6:"errmsg";
s:15:"Invalid card #.";s:8:"function";s:5:"CCVal";}
s:9:"aSubNodes";a:0:{}}i:2;O:7:"xmlnode":3:
s:5:"sName";s:11:"vlvalidator";s:6:"aAttrs";a:5:
{s:4:"name";s:18:"CardNumberNumCheck";s:4:"
type";s:9:"checktype";s:7:"control";s:10:"
CardNumber";s:6:"errmsg";s:15:"Invalid card #.";s:9:
"validtype";s:7:"integer";}s:9:"aSubNodes";a:0:
{}}i:3;O:7:"xmlnode":3:{s:5:"sName";s:11:"
vlvalidator";s:6:"aAttrs";a:4:{s:4:"name";s:13:
"CurrentPINReq";s:4:"type";s:8:"required";s:7:
"control";s:10:"CurrentPIN";s:6:"errmsg";s:21:
"Current PIN required.";}s:9:"aSubNodes";a:0:{}}i:4;O:7:
"xmlnode":3:{s:5:"sName";s:11:"vlvalidator";
s:6:"aAttrs";a:5:{s:4:"name";s:16:"
CurrentPINRegExp";s:4:"type";s:6:"regexp";s:7:
"control";s:10:"CurrentPIN";s:6:"errmsg";
s:20:"Invalid Current PIN.";s:6:"regexp";
s:9:"/^\d{4}$/";}s:9:"aSubNodes";a:0:{}}}}" />
</form>
</body>
</html>
'Phishing' links:
How Not to Get Hooked by a �Phishing� Scam
Anti-Phishing Working groups
eBay Security Center
spoof@ebay.com (eBay spoof reporting address)
Citibank: Citi ™ Cards – Security and You
Anti-Spam Resources:
jwSpamSpy is our spam filter (free evaluation version available for download)
Anti-spam domain blacklist – list of domains that I refuse to receive mail from
Recent additions to domain blacklist (with whois details)
"419" scam sender/contact addresses ("Nigeria connection" address book)
Plain text versions of the domain and 419 blacklist
Domain blacklist update (DBL-Update) archive
About the 419 (Advance Fee) scam
DNS-based IP and domain name blacklists
IP address ranges
Dynamic IP addresses (700 KB!)
Name server / Registrar combinations
Free email providers
AOL dial-up address ranges and mail servers
How to trace senders of spam
Frequently asked questions (FAQ)
Lookup an IP address on blacklists (http://dnsbl.net.au/lookup/)
Clueless virus filters spam innocent third parties
Challenge and Response spam filters: A selfish idea for selfish times
ShareYourExperiences.com spammers
Smyrnagroup spammers (in German)
Kaplan College spam
Stock Price Manipulation Spam ("Pump & Dump")
What's the deal with "OEM software"?
'Phishing' for your wallet (Fraud)
Job offer spam: Processing payments (Fraud)
Forwarding Paypal payments via Western Union (Fraud)
Spam phone numbers ("diploma" spam, etc.)
"Joe job" information
Link exchange offer spam
Getting creative with spam
Link exchange spam: allcarpictures.com
Xenophobia, Spam and Viruses: The "German Spam" (Sober.H)
Sober.H – Racist German email spam spread by virus (in German)
"Joe job" against joewein.de
Porn spam: watchsound.com
Porn spam: hotsalza.com
Name servers used by spammers: joker.com
Rogue name servers: mediadreamland.com
Rogue name servers: airmaramba.biz
Rogue name servers: bonafidecash.com
Rogue name servers: maileasy.biz
Browser hijacking: heretofind.com
Domain Blacklist Archive:
2004-11:
01
02
03
04
05
06
07
08
09
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
2004-10:
01
02
03
04
05
06
07
08
09
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
2004:
Jan,
Feb,
Mar,
Apr,
May,
Jun,
Jul,
Aug,
Sep,
Oct,
Nov
2003:
Oct,
Nov,
Dec